Mental Health Facility Vendor Risk Management: Privacy, Safety, and Specialized Care
Post Summary
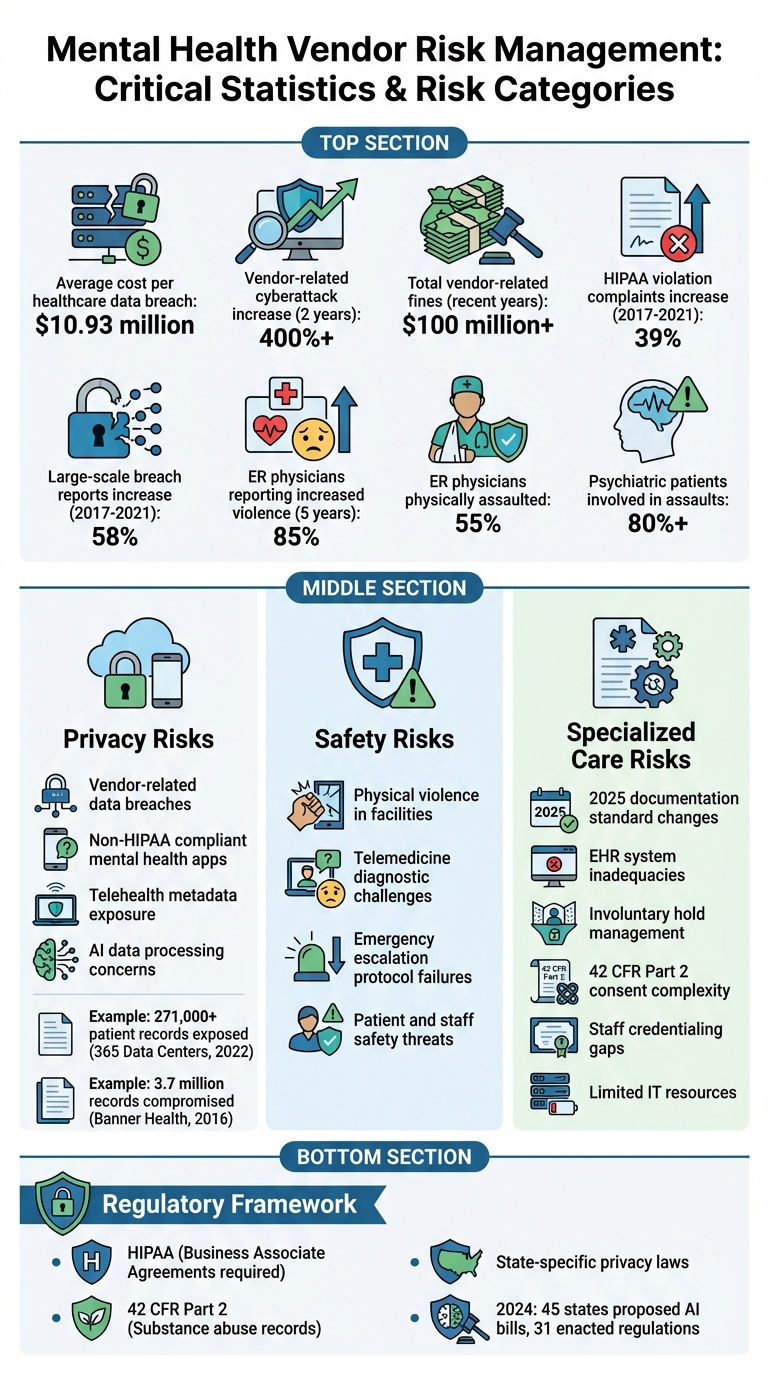
Mental health facilities face unique challenges when managing vendor risks, especially when handling sensitive patient data like therapy notes and substance abuse records. With rising data breaches in healthcare - costing an average of $10.93 million per incident - vendor oversight is critical to protect patient privacy, ensure safety, and maintain compliance with strict regulations like HIPAA and 42 CFR Part 2.
Key takeaways:
- High stakes: Mental health data breaches can shatter patient trust and disrupt care.
- Regulations: HIPAA and 42 CFR Part 2 require strict data safeguards and consent protocols.
- Vendor risks: Privacy breaches, safety concerns, and specialized care failures are top concerns.
- Solutions: Effective vendor risk management includes security assessments, compliance monitoring, and clear contracts.
Facilities must prioritize vendor risk programs to safeguard privacy, ensure safety, and support patient care while navigating an increasingly complex regulatory landscape.
Mental Health Vendor Risk Management: Key Statistics and Risk Categories
Regulatory and Ethical Requirements for Vendor Risk Management
Required Regulatory Compliance
Protecting sensitive mental health data hinges on meeting regulatory demands and maintaining ethical standards in vendor relationships. Mental health facilities must navigate a complex web of regulations while ensuring vendors uphold these standards.
At the core of these requirements is HIPAA, which mandates that facilities establish Business Associate Agreements (BAAs) with any vendor that handles Protected Health Information (PHI) [2]. These agreements must clearly outline how PHI will be used, include strict safeguards, define subcontractor responsibilities, grant audit rights, require breach notifications, and specify termination procedures.
For facilities subject to additional rules, like 42 CFR Part 2, consent protocols come into play. State laws often add another layer of complexity, requiring both facilities and their vendors to meet evolving standards [1]. A key step in managing compliance is vendor classification - determining whether a vendor is a Business Associate or Non-Business Associate based on their access to PHI. This classification dictates the level of due diligence required and whether a BAA is necessary [2].
Ethical Considerations in Vendor Oversight
Regulations alone aren't enough - mental health facilities also have ethical responsibilities in their vendor relationships. Ethical principles such as patient autonomy, beneficence, nonmaleficence, justice, fidelity, and veracity guide these decisions [6]. These principles translate into actionable practices: vendors should uphold patient dignity, maintain confidentiality, and handle data in ways that reduce stigma.
When choosing technology vendors, facilities should prioritize those that demonstrate a commitment to improving patient outcomes. This might include vendors whose tools integrate seamlessly with established therapy models or those that enhance access to care through features like single sign-on or Employee Assistance Program (EAP) integration [7]. By applying this ethical lens, facilities can ensure vendor partnerships align with their therapeutic goals and actively support patient well-being.
Applying Compliance and Ethics to Vendor Selection
Turning regulatory and ethical requirements into practical vendor selection criteria requires a structured approach. During onboarding, facilities should use detailed security questionnaires and verify certifications like HIPAA, HITRUST, and SOC 2 Type II [2][4][7].
Contracts should clearly define expectations for data protection, confidentiality, security, and exit strategies. For Business Associates, BAAs must include "flow-down" clauses, ensuring subcontractors uphold the same protections as primary vendors [2]. Ongoing monitoring - through periodic security assessments, performance attestations, and audits - helps maintain compliance and reduces third-party risk [2]. When a vendor relationship ends, secure offboarding processes are critical. This includes ensuring all PHI is returned or destroyed and promptly revoking access to prevent data exposure [2].
Types of Risk in Mental Health Vendor Relationships
Mental health facilities face several vendor-related risks that can jeopardize both patient privacy and the quality of care. These risks generally fall into three main categories.
Privacy Risks
Mental health data is particularly sensitive, and breaches can have far-reaching consequences. Recent years have seen a rise in vendor-related attacks, resulting in over $100 million in fines[5][9]. Between 2017 and 2021, complaints about HIPAA violations jumped by 39%, while reports of large-scale breaches increased by 58%[10].
A significant concern is that many mental health apps and platforms don’t fall under HIPAA regulations, leading to weaker data protection measures. Telehealth vendors, for example, often collect metadata that could potentially be misused to infer treatment details or diagnoses. In 2024 alone, 45 states proposed AI-related bills, and 31 states enacted new AI regulations[8].
"The vast amount of data that AI has access to and how it processes it, the speed at which it processes it, and the way it could affect care, even at an augmented level, means there's always a concern. This is very private data, and you want the AI to use it in a responsible way." – Rony Gadiwalla, CIO of GRAND Mental Health[8]
Real-world examples illustrate the risks. In December 2022, a breach at 365 Data Centers exposed the medical records of over 271,000 patients of Avem Health Partners[11]. Similarly, in 2016, hackers accessed Banner Health’s network through a third-party food court payment processor, compromising 3.7 million records[5]. Beyond privacy, vendor failures can directly threaten the safety of patients and staff.
Safety Risks
Vendor issues don’t just stop at privacy - they can also affect physical safety. A 2022 survey by the American College of Emergency Physicians revealed that 85% of ER physicians had seen a rise in violence in emergency departments over the past five years. Of those surveyed, 55% reported being physically assaulted, with psychiatric patients accounting for over 80% of these incidents[12].
Telemedicine introduces its own safety challenges. Without in-person interaction, diagnostic accuracy and patient trust can suffer. This makes reliable communication systems and clear escalation protocols essential when addressing emergencies.
Specialized Care Risks
Vendors must also meet the unique demands of mental health care, which adds another layer of complexity. Starting in 2025, new documentation standards will require more detailed, audit-ready records. Vendors providing electronic health record (EHR) systems must ensure their platforms can handle these requirements effectively[1]. Systems that lack expertise in behavioral health may fall short in areas like managing involuntary holds, documenting seclusion and restraint incidents, or adhering to the nuanced consent protocols outlined in 42 CFR Part 2.
Telehealth vendors face additional hurdles, including compliance with specific licensing, billing, and consent requirements[1]. Proper staff credentialing is another critical factor, as behavioral health care often involves specialized certifications and ongoing training - features that general-purpose systems might not track well.
Behavioral health facilities are frequent targets for cyberattacks, yet they often operate with limited resources and overextended IT teams. Vendors need to offer scalable security measures, such as encrypted communication, routine vulnerability scans, and tailored phishing awareness programs, to protect these organizations and their sensitive data[1].
Creating a Vendor Risk Management Program for Mental Health Facilities
Building a vendor risk management program for mental health facilities requires tailoring risk processes to safeguard sensitive data, maintain safety, and support specialized care. Start by identifying and categorizing vendors based on their access to Protected Health Information (PHI). This helps facilities focus their efforts on high-risk vendors - those essential to patient care or those handling PHI. By prioritizing risks tied to privacy, safety, and specialized care, this structured approach connects standard vendor risk management practices to the unique needs of mental health care.
Tailoring the Vendor Risk Lifecycle
In mental health environments, every stage of the vendor risk lifecycle must address privacy concerns, patient safety, and specialized care requirements. Before onboarding, evaluate vendors using detailed questionnaires that focus on compliance with HIPAA and state-specific privacy laws. Pay extra attention to telehealth vendors, ensuring they meet licensing requirements across states, secure proper informed consent, and adhere to accurate billing practices[1][11].
Conduct thorough risk assessments before onboarding and include strong data protection clauses in contracts. These should address confidentiality, security, and provide clear exit strategies. During onboarding, verify critical details like cybersecurity certifications, insurance coverage, and staff credentials for vendors managing sensitive data. Automated onboarding systems can help collect comprehensive risk data efficiently[5].
Using Technology for Vendor Risk Management
Mental health facilities often face resource constraints and stretched IT teams, making technology a vital tool for scaling risk management. Technology platforms can streamline vendor oversight while complementing earlier mitigation efforts. For example, Censinet RiskOps™, an AI-powered cloud platform, enhances patient safety by reducing cyber risks. It facilitates secure sharing of cybersecurity and risk data across a network of healthcare organizations and over 50,000 vendors and products[13][14].
Another tool, Censinet AITM, speeds up third-party risk assessments. Vendors can complete security questionnaires in seconds, and the platform automatically summarizes evidence, captures product integration details, identifies fourth-party risks, and generates risk summary reports. This automation allows risk teams to handle complex issues more efficiently while maintaining oversight and precision[16].
Continuous Monitoring Practices
To keep the program effective, implement continuous monitoring that builds on earlier compliance and risk assessment efforts. Use real-time cybersecurity monitoring, conduct regular audits, and evaluate fourth-party risks to ensure the entire vendor network remains secure. A 2022 Ponemon Institute report revealed that ransomware attacks in healthcare caused severe disruptions, including increased patient mortality, delayed treatments, and prolonged hospital stays[15].
Prepare for potential incidents by establishing clear response protocols to address security breaches or service failures quickly. When contracts end, follow a detailed offboarding process: revoke vendor access permissions, update passwords, and confirm the secure destruction of patient data. These steps help maintain the integrity of your risk management program and protect sensitive information.
sbb-itb-535baee
Governance, Metrics, and Program Improvement
When it comes to vendor risk management in mental health facilities, having strong governance and measurable outcomes is non-negotiable. A solid governance framework ensures that the right people, processes, and goals are aligned, creating a foundation for effective decision-making. Without this structure, risk management efforts can falter at crucial moments.
Setting Up Governance Structures
Strong governance starts with assembling committees that include experts in IT security, compliance, clinical operations, and privacy. Begin by outlining clear objectives - whether it’s reducing risks, improving performance, meeting compliance standards, or controlling costs. Once the goals are clear, map out the vendor lifecycle, incorporating key checkpoints like pre-onboarding security reviews and annual risk reassessments.
To streamline operations, create standardized documents for vendor due diligence, contracts, service level agreements (SLAs), risk assessments, and escalation protocols. Selecting the right governance model is also crucial. Centralized frameworks work best in highly regulated environments by promoting consistency and quicker decision-making. On the other hand, decentralized models allow more autonomy but can risk fragmentation. A hybrid approach blends centralized control with decentralized execution, offering a balance between oversight and flexibility [17]. These governance structures not only ensure initial risk assessments are thorough but also lay the groundwork for continuous improvement, strengthening the facility’s cybersecurity defenses.
Metrics and Risk Indicators
Once governance is in place, tracking meaningful metrics becomes the next step in refining risk management. These metrics provide a clear picture of whether the vendor risk program is achieving its goals. Focus on indicators that align with privacy protection, safety, and the unique needs of mental health care. Examples include the percentage of high-risk vendors assessed, the average time taken to resolve vulnerabilities, and the number of vendor-related security incidents.
To ensure consistency, establish measurement strategies tied to SLAs and document the processes so they can be easily replicated. Risk profiles should be updated regularly, especially when new technologies are adopted, security incidents occur, or there are shifts in the business environment [18][19]. Continuous risk analysis ensures that the program remains responsive to changing conditions [3].
Technology Tools for Risk Governance
Technology can turn what is often a manual and time-consuming governance process into a streamlined, efficient operation. Platforms like Censinet RiskOps™ provide real-time visibility across the vendor network. With features like dashboards that aggregate risk data, governance committees can quickly access the information they need to make informed decisions.
The platform also offers robust reporting tools, delivering regular updates to senior management and boards on vendor risks, performance trends, and security incidents. Automated workflows route critical findings to the appropriate stakeholders, ensuring timely action. This level of oversight not only boosts accountability but also simplifies the management of risk-related policies, procedures, and tasks. Acting as a centralized hub, Censinet RiskOps™ supports compliance efforts while driving ongoing improvements across the vendor ecosystem.
Conclusion: Protecting Privacy, Safety, and Specialized Care
Vendor risk management in mental health facilities goes far beyond ticking off compliance checklists - it's about safeguarding the privacy and well-being of some of the most vulnerable individuals and their sensitive information. The stakes are undeniably high. For instance, mental health facilities face distinct challenges, such as preserving the integrity of therapeutic relationships in telehealth and ensuring subcontracted staff are adequately trained to handle confidential mental health data.
The financial and operational risks of falling short in vendor risk management are immense. Healthcare organizations, on average, incur nearly $10 million in costs per data breach, and vendor-related cyberattacks have skyrocketed by over 400% in just two years [5]. These figures highlight why having a thoughtful, tailored approach to vendor risk management is no longer optional - it's a necessity in today’s increasingly complex threat environment.
To address these challenges, effective vendor risk management demands strong governance, measurable outcomes, and technology that simplifies and centralizes processes. For example, advanced risk management platforms now offer real-time insights, automated workflows, and centralized oversight, making it easier for facilities to stay proactive.
Looking ahead, mental health facilities will face even greater pressures as we approach 2025. From stricter data privacy regulations to evolving telehealth compliance standards and growing cybersecurity threats, the regulatory landscape is becoming more demanding [1]. Facilities that prioritize comprehensive vendor risk management programs today will be better positioned to adapt to these shifts, maintaining patient trust while navigating these complexities.
The way forward is clear: combine rigorous compliance with ethical decision-making, supported by scalable technology and continuous monitoring. This approach ensures patient privacy, reinforces safety, and upholds the specialized care that lies at the core of mental health services. Strategic investments now will pave the way for a resilient future in mental health care.
FAQs
What are the key risks when working with vendors in mental health facilities?
Vendors working with mental health facilities can bring about serious risks. These risks include violations of patient privacy, weaknesses in data security, and failure to meet healthcare regulations such as HIPAA. On top of that, operational missteps or a lack of proper safety protocols can compromise patient care and disrupt facility operations.
Because mental health data is highly sensitive and requires specialized handling, it's crucial to carefully evaluate and address vendor-related risks. This ensures patient information stays protected while maintaining secure and compliant working relationships.
What steps can mental health facilities take to comply with HIPAA and 42 CFR Part 2 regulations?
To align with HIPAA and 42 CFR Part 2 regulations, mental health facilities must actively work to safeguard sensitive patient information and uphold compliance standards. Start by performing detailed risk assessments to uncover any weaknesses in how data is handled, stored, or shared.
Put strong physical and technical protections in place, such as encryption, access controls, and secure data storage systems. Make sure all vendors who manage patient information sign Business Associate Agreements (BAAs) and strictly follow compliance rules. It’s equally important to create clear policies for staff, offer regular training on privacy protocols, and routinely monitor compliance efforts to address any vulnerabilities or risks.
Taking these measures not only helps protect patient privacy but also ensures facilities meet the specific requirements of mental health care environments.
Why is continuous monitoring essential for managing vendor risks in mental health facilities?
Continuous monitoring plays a key role in managing risks tied to patient privacy, safety, and meeting regulatory standards in real time. Mental health facilities deal with extremely sensitive information, making any data breach or lapse a serious issue with potentially far-reaching impacts on both patients and the organization.
By routinely evaluating vendor performance and security protocols, these facilities can address new threats swiftly, stay aligned with healthcare regulations, and uphold trust in their operations. This forward-thinking strategy protects patient data and ensures the secure environment necessary for providing specialized care.


